
The ERMAC Android banking trojan has released version 2.0, increasing the number of applications targeted from 378 to 467, covering a much wider range of apps to steal account credentials and crypto wallets.
The goal of the trojan is to send stolen login credentials to threat actors, who then use them to take control of other people’s banking and cryptocurrency accounts and conduct financial or other forms of fraud.
ERMAC is currently sold to members of darknet sites at a subscription rate of $5,000 per month, which is $2k over the price tag of the first version, reflecting the upgrade in features and its popularity.
Fake Bolt Food app
The first malware campaign utilizing the new ERMAC 2.0 malware is a fake Bolt Food application targeting the Polish market.
According to ESET researchers, the threat actors distributed the Android app through the “bolt-food[.]site” website, impersonating the legitimate European food delivery service. This fake site is still up at the time of this writing.
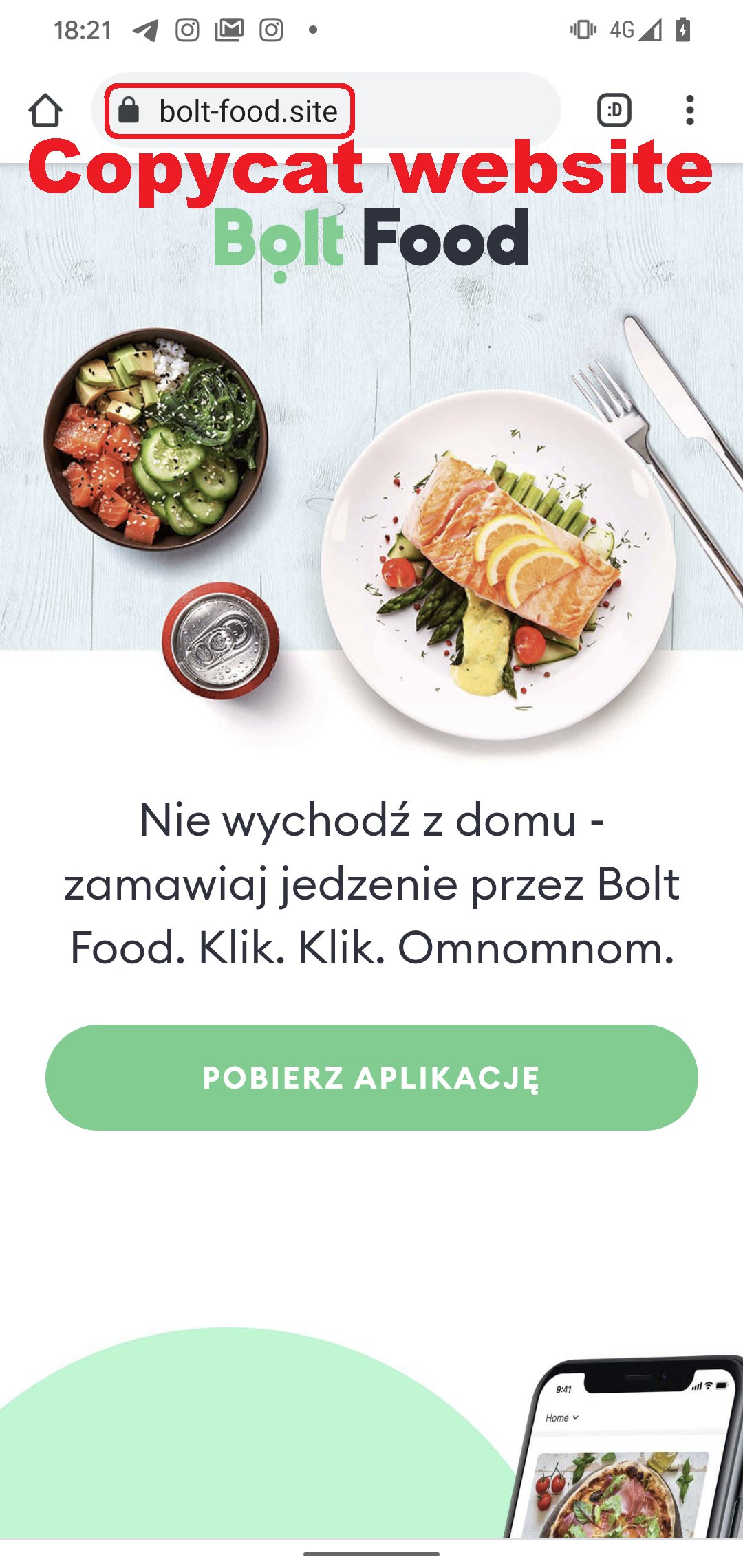
Users likely end up on the fake site via a phishing email, malicious social media posts, smishing, malvertising, etc. If they download the app, they are met with a permission request that demands complete control of their device.
.jpg)
(ESET)
Granting access to the Accessibility Service is required to serve the application overlays, tricking the victim into entering their credentials on forms that look legitimate but are just clones of the actual application interfaces.
Cyble has sampled the malware for a deeper technical analysis and confirms that it grants itself 43 permissions upon installation (via Accessibility), including SMS access, contact access, system alert window creation, audio recording, and full storage read and write access.
Targeting a galore of apps
ERMAC first determines what applications are installed on the host device and then sends the information to the C2 server.
The response contains the injection modules that match the application list in encrypted HTML form, which the malware decrypts and stores into the Shared Preference file as “setting.xml.”
.png)
When the victim attempts to launch the real application, the injection action occurs, and a phishing page is loaded on top of the actual GUI. The harvested credentials are sent to the same C2 that provided the injections.
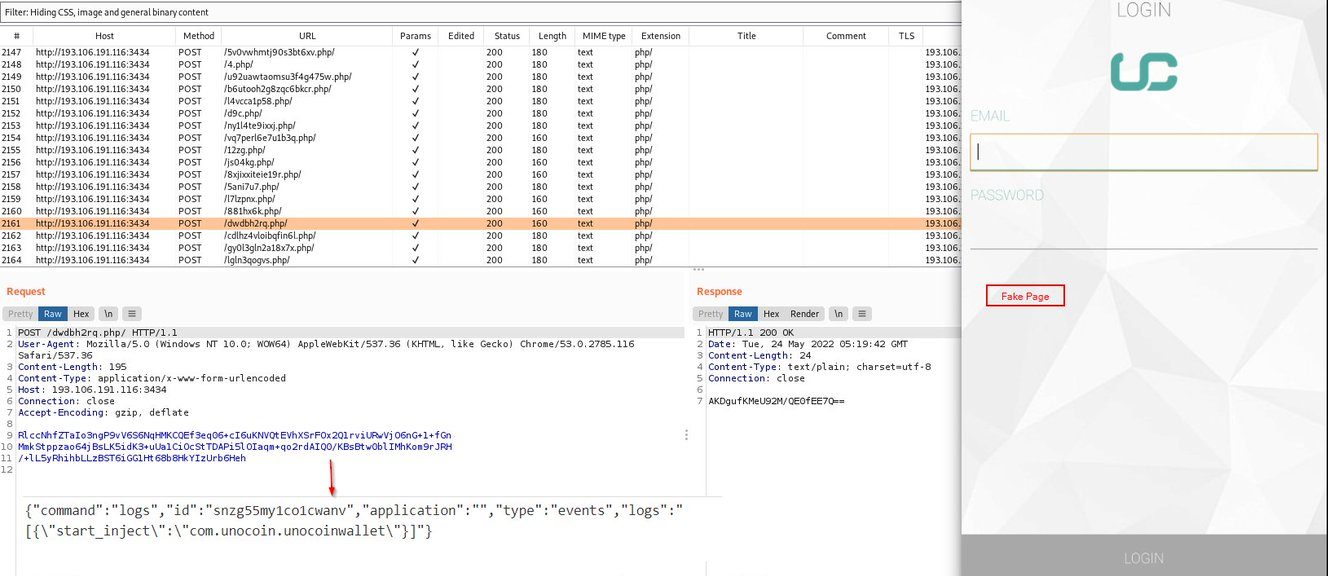
The commands supported by ERMAC 2.0 are the following:
- downloadingInjections – Sends the application list to download injections
- logs – Sends injection logs to the server
- checkAP – Check the application status and send it to the server
- registration – Sends device data
- updateBotParams – Sends the updated bot parameters
- downloadInjection – Used to receive the phishing HTML page
The banking apps targeted by EMAC 2.0 include institutions worldwide, making the app suitable for deployment in many countries. Moreover, popular cryptocurrency wallets and asset management apps are stolen too.
Cyble’s analysts have found many similarities to the “Cerberus” malware, so it appears that the second version of the powerful trojan is based on it.
The extensive list of apps supported make this a potent malware, but it’s worth noting that it would stumble into problems in Android versions 11 and 12, thanks to the additional restrictions that Google added to prevent Accessibility Service abuse.
To prevent infections from Android trojans, avoid downloading APKs from outside the Play Store, especially from websites you haven’t confirmed as legitimate.



Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now