
The Industrial Spy data extortion marketplace has now launched its own ransomware operation, where they now also encrypt victim's devices.
Last month, we reported on a new data extortion marketplace called Industrial Spy that allowed threat actors, and possibly even business competitors, to purchase data stolen from companies.
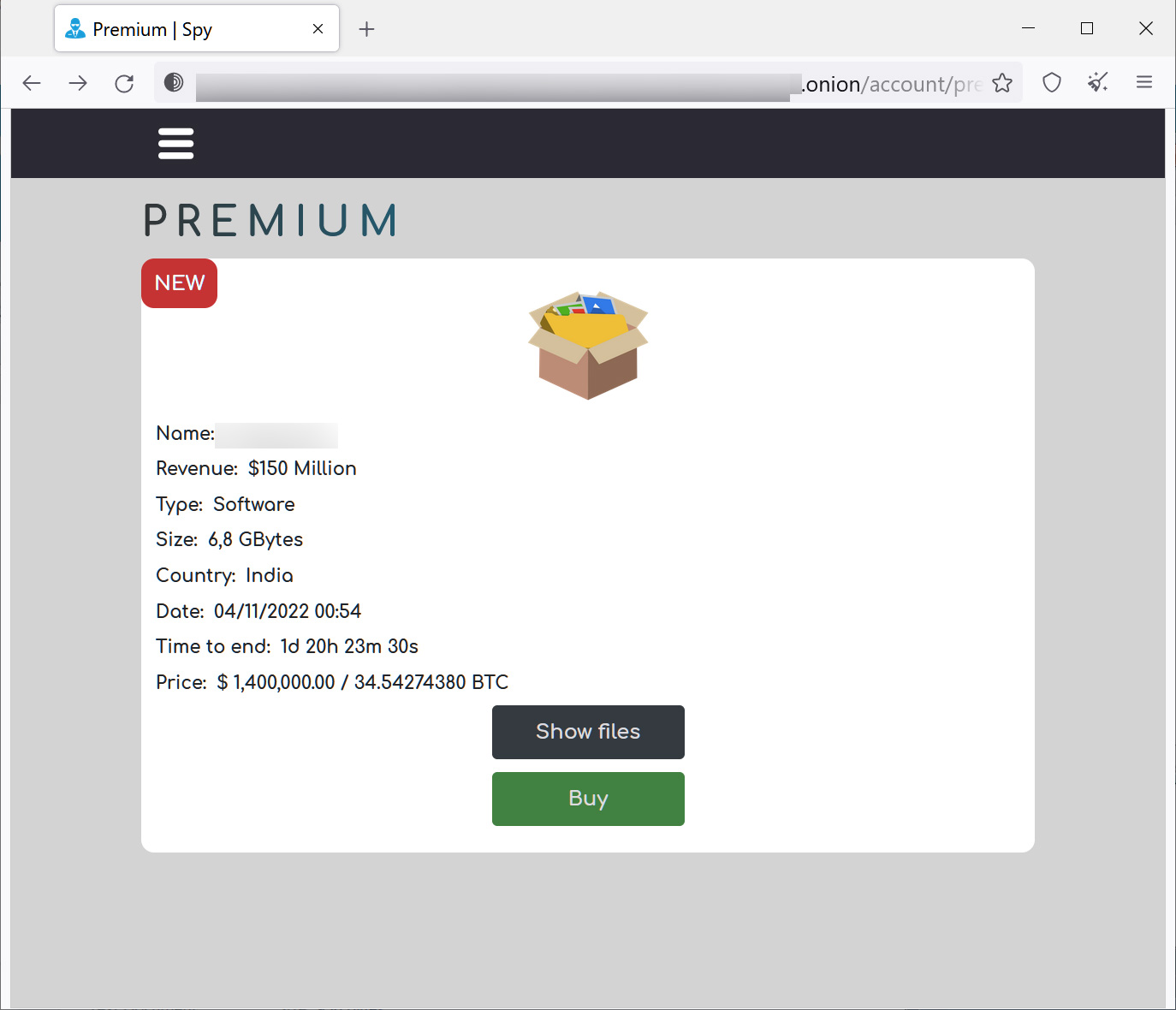
This marketplace sells different types of stolen data, ranging from selling 'premium' data for millions of dollars to individual files for as little as $2.
Source: BleepingComputer
To promote their service, the threat actors partnered with adware loaders and fake crack sites to distribute malware that would create README.txt files on a device.
The threat actors used these files to promote their marketplace, explaining that readers can purchase schemes, drawings, technologies, political and military secrets, accounting reports, and client databases of their competitors.
Industrial Spy gets into the ransomware game
Last week, security researcher MalwareHunterTeam found a new sample of the Industrial Spy malware with what looked more like a ransom note rather than a promotional text file.
This ransom note now states that the Industrial Spy threat actors not only stole the victim's data but also encrypted it.
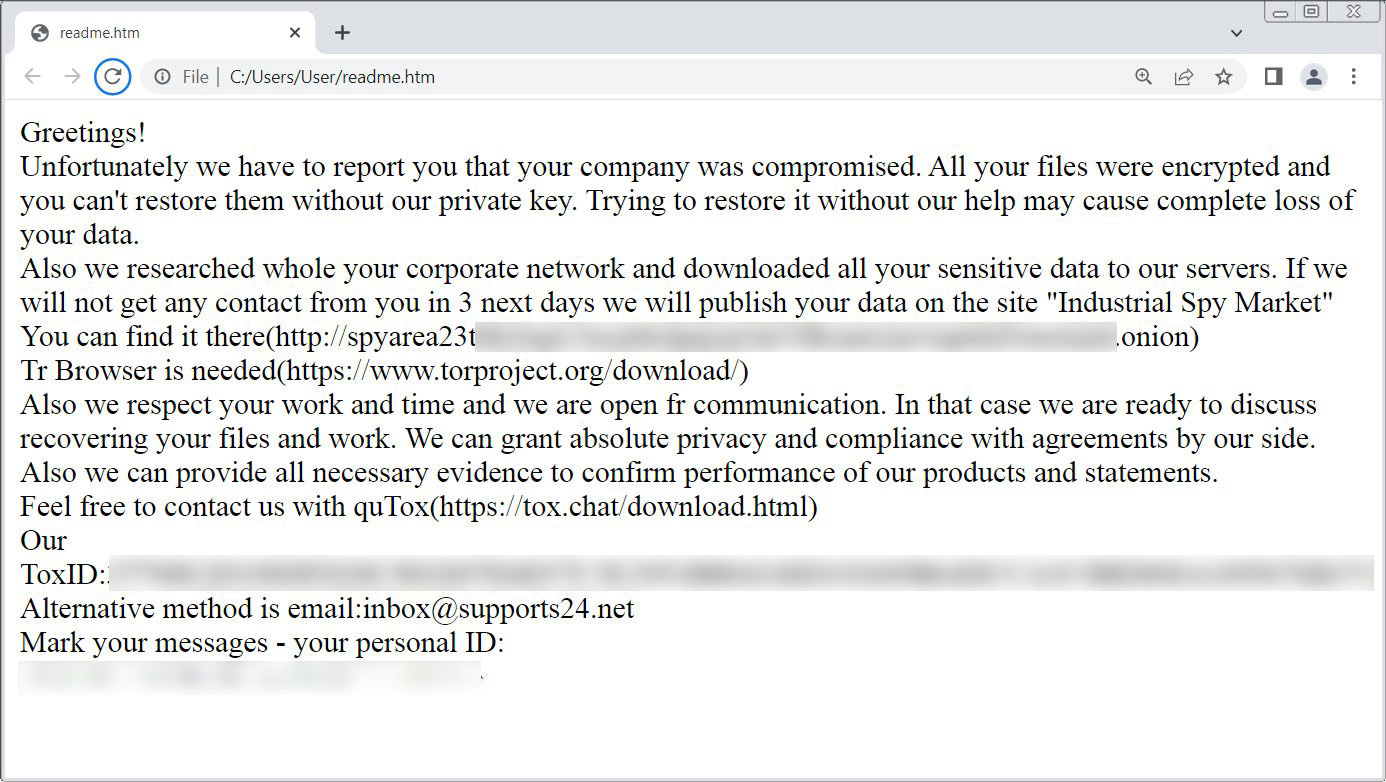
"Unfortunately we have to report you that your company was compromised. All your files were encrypted and you can't restore them without our private key. Trying to restore it without our help may cause complete loss of your data," reads the Industrial Spy ransom note shared below.
"Also we researched whole your corporate network and downloaded all your sensitive data to our servers. If we will not get any contact from you in 3 next days we will publish your data on the site 'Industrial Spy Market'."
Source: BleepingComputer
MalwareHunterTeam shared the malware sample with BleepingComputer to confirm if it encrypted files as it said.
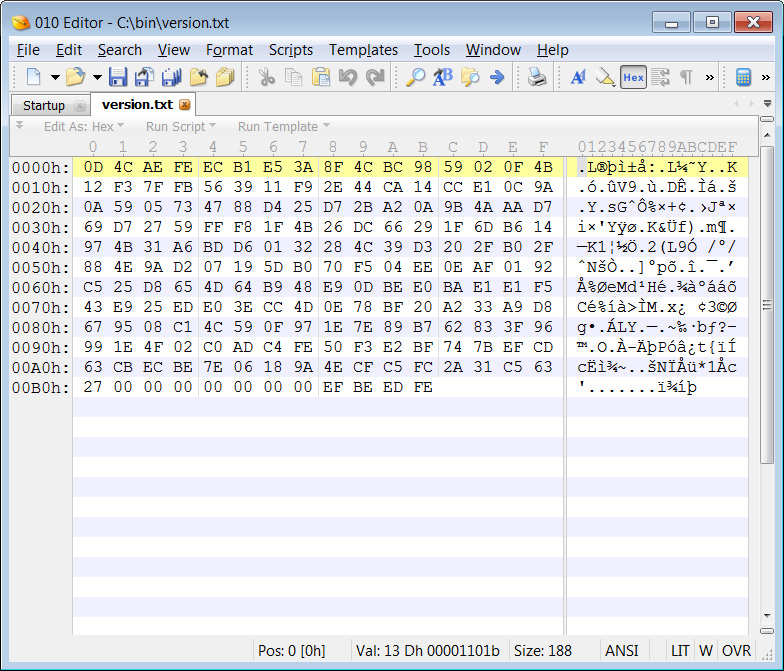
BleepingComputer's tests showed that the Industrial Spy ransomware does indeed encrypt files, but unlike most other ransomware families, does not append a new extension to encrypted file's names, as shown below.
Source: BleepingComputer
BleepingComputer also shared the sample with ransomware expert Michael Gillespie, who said from a glance that he believes that it uses DES encryption, with the key encrypted using an RSA1024 public key.
The ransomware also uses a filemarker of 0xFEEDBEEF, which we have not seen before in a ransomware family. However, this filemarker should not be confused with 0xDEADBEEF; a well-known magic debug value used in programming.
While encrypting files, the Industrial Spy ransomware will create the above ransom note named 'README.html' in every folder on the device.
These ransom notes contain a TOX id that victims can use to contact the ransomware gang and negotiate a ransom.
A tie to Cuba ransomware?
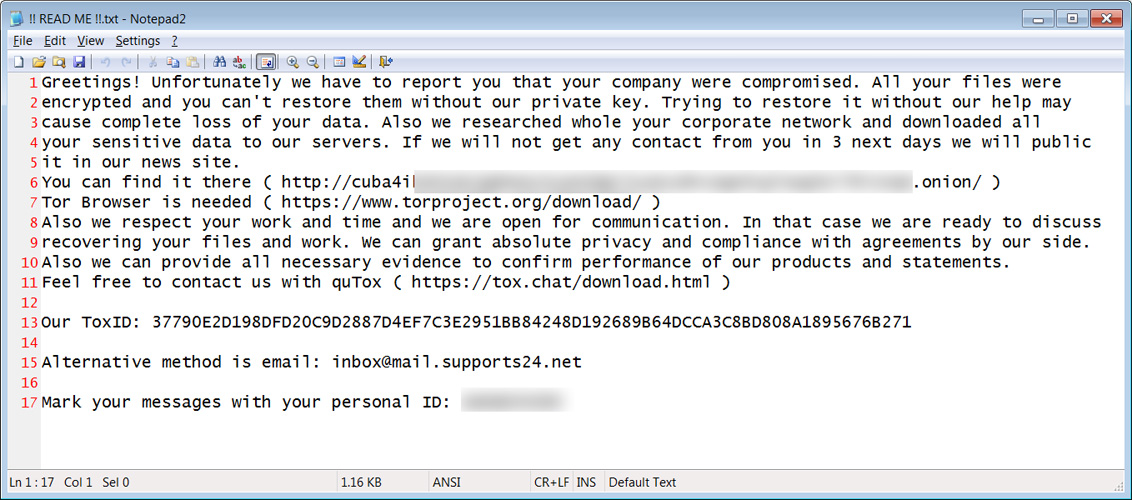
When researching the TOX ID and email address found in the ransom note, MalwareHunterTeam discovered a strange connection to the Cuba ransomware operation.
A ransomware sample uploaded to VirusTotal creates a ransom note with an identical TOX ID and email address. However, instead of linking to the Industrial Spy Tor site, it links to Cuba Ransomware's data leak site and uses the same file name, !! READ ME !!.txt, as known Cuba ransom notes.
Source: BleepingComputer
Furthermore, the encrypted files have the .cuba extension appended to them, just like the regular Cuba ransomware operation does when encrypting files.
While this does not 100% tie the two groups together, it's very possible that the Industrial Spy threat actors simply used Cuba's information while testing the creation of their ransomware.
However, it is peculiar and something that security researchers and analysts will need to keep an eye on.


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now